Introduction
The Zero Trust model, assumes that no user, device, or application—whether inside or outside the network—can be trusted without verification and has become essential for modern organisations. Microsoft Intune, as part of Microsoft’s Endpoint Manager, offers powerful tools to implement a Zero Trust framework. In this blog post, we’ll explore how Microsoft Intune can be used to achieve a robust Zero Trust architecture.
What is Zero Trust Security?
At its core, Zero Trust assumes that trust should never be implicit. Every access request is treated as potentially malicious, and users, devices, and applications must consistently prove they meet specific security standards. The key principles of Zero Trust include:
- Verify explicitly – Always authenticate and authorize based on all available data points, such as user identity, location, device health, etc.
- Use least privilege access – Limit access to resources to only what is necessary for users to perform their tasks.
- Assume breach – Continuously monitor and analyse for malicious activity and be prepared for a security breach at any time.
How Microsoft Intune Supports Zero Trust
Microsoft Intune is a cloud-based service that focuses on mobile device management (MDM) and mobile application management (MAM). By leveraging Intune, organizations can control how devices are used, enforce security policies, and ensure devices comply with corporate standards before they can access resources. Here’s how Microsoft Intune can help in implementing the core principles of Zero Trust:
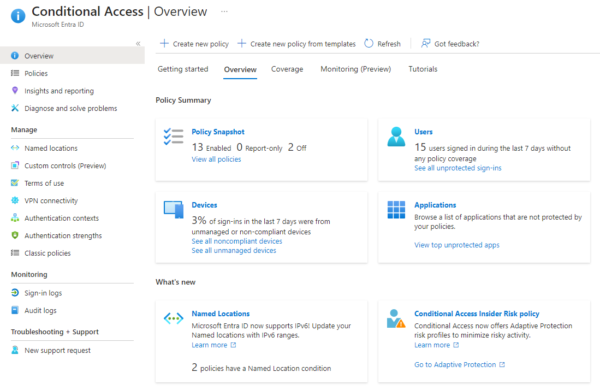
Verify Identity and User Access with Conditional Access Policies
The first pillar of Zero Trust is to explicitly verify users and devices. Microsoft Intune integrates deeply with Azure Active Directory (Azure AD) to enforce Conditional Access policies, ensuring only authenticated and authorized users can access sensitive data.
- Conditional Access – Policies can be tailored to require multi-factor authentication (MFA) when accessing resources based on user role, device status, or location. For example, a user trying to access corporate data from a new device or an untrusted location may be prompted to complete an additional MFA step.
- Device compliance checks – Before granting access, Intune can enforce device compliance checks. Devices must meet specific security requirements, such as being encrypted, up-to-date with patches, and not jailbroken or rooted, ensuring only secure devices can connect.
Example: A user attempting to access company email from a mobile device may be prompted to authenticate with MFA, and Intune will check whether the device is encrypted and compliant with corporate policies before granting access.
Implement Device Compliance Policies
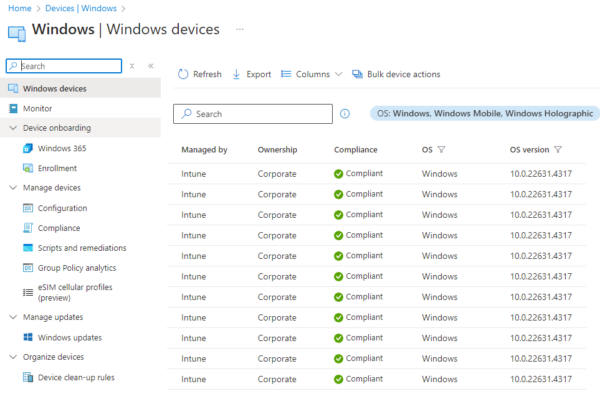
Zero Trust emphasises that every device attempting to access corporate resources must be verified and trusted. Microsoft Intune offers comprehensive tools to assess the health of devices, manage compliance, and remediate issues automatically.
- Device compliance policies – Administrators can create compliance policies for different platforms (Windows, iOS, Android) to ensure devices meet security standards. These policies can include requirements for:
- OS version control (devices must be updated to the latest version).
- Encryption (data on devices must be encrypted to protect against unauthorized access).
- Secure passwords (enforcing strong passwords with complexity rules).
- Compliance reporting – Microsoft Intune provides dashboards that show the compliance status of all managed devices, helping IT admins quickly identify and address non-compliant devices.
Example: A laptop attempting to access internal systems will be checked for compliance. If it’s found to be out of date or missing a security patch, access can be blocked until the device is updated.
Endpoint Protection with Mobile Threat defence (MTD)
Intune can also be integrated with Mobile Threat defence (MTD) solutions like Microsoft Defender for Endpoint. This ensures that the health and security of devices are monitored in real-time, and malicious activity is detected and mitigated proactively.
- Real-time threat detection – MTD solutions can identify malware, suspicious activity, or security misconfigurations on devices. These risks are automatically reported back to Intune, which can adjust device compliance status accordingly.
- Automated remediation – If a device is compromised, Intune can restrict access to corporate resources immediately and enforce remediation steps (e.g., requiring the device to run a virus scan or update its security patches).
Example: If malware is detected on a user’s smartphone, Intune can immediately quarantine the device, preventing it from accessing any sensitive information until the threat is resolved.
Application Security with App Protection Policies
In a Zero Trust environment, it’s essential to protect corporate data, not only on devices but also within specific applications. Intune’s App Protection Policies allow organisations to secure the apps where sensitive data resides, regardless of whether the device is managed.
- Data loss prevention (DLP) – App protection policies can enforce restrictions such as blocking the copy/paste of data between personal and work apps, requiring encryption of app data, or ensuring that apps are accessed only from trusted devices.
- Selective wipe – If a device is lost or an employee leaves the company, administrators can remotely wipe only corporate data from apps, leaving personal information intact.
Example: A remote employee using Microsoft Word on their personal device to work on a sensitive company document will be subject to App Protection Policies. These policies ensure that the document cannot be copied into personal apps or shared through unsecured channels.
Limit Access with Least Privilege and Role-Based Access Control (RBAC)
Another key principle of Zero Trust is to grant users only the access they need to perform their jobs. Microsoft Intune supports this with Role-Based Access Control (RBAC).
- Customised roles – Administrators can create roles with specific permissions, ensuring users only access the parts of Intune (or other corporate resources) that are relevant to their role.
- Granular access control – Access to specific applications, data, or devices can be restricted based on a user’s identity, job role, or location, ensuring least-privilege access.
Example: An IT support technician may have access to manage devices within Intune but won’t have the permissions needed to access sensitive financial data stored in corporate apps.
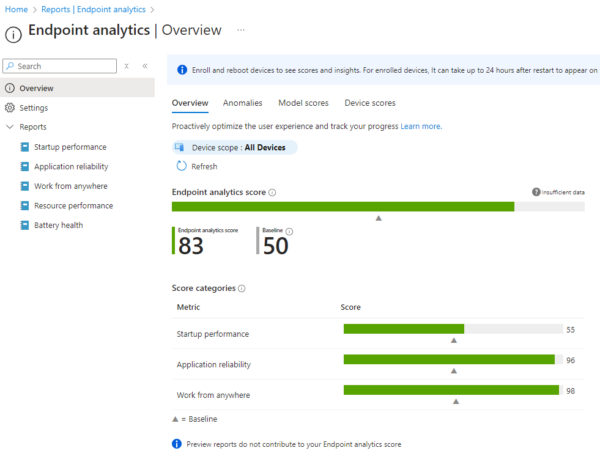
Continuous Monitoring and Reporting
Finally, Zero Trust emphasises the importance of continuous monitoring to detect threats in real-time. Microsoft Intune integrates with tools like Microsoft Defender for Endpoint and Azure Sentinel to provide comprehensive monitoring across the entire digital estate.
- Security alerts – Integration with Azure Sentinel provides a centralised view of security events and incidents, allowing teams to detect, investigate, and respond to threats more effectively.
- Detailed reporting – Intune’s built-in reporting features give administrators detailed insight into device compliance, security threats, and app usage, enabling them to make informed decisions about security policies.
Example: An admin can monitor the compliance and security posture of all managed devices in real-time, ensuring any potential security risks are flagged and addressed promptly.
Achieving Zero Trust with Microsoft Intune
Microsoft Intune is a powerful tool for implementing Zero Trust security across devices, apps, and data. By leveraging its capabilities—like Conditional Access, device compliance checks, app protection policies, and continuous monitoring—organisations can ensure that every user, device, and application is authenticated, authorised, and secure before accessing corporate resources.
Adopting a Zero Trust approach with Intune not only strengthens security but also enhances agility, making it easier to manage a distributed, mobile, and remote workforce without compromising on protection. If your organisation is considering Zero Trust, Intune offers a scalable, flexible platform to make it happen.
To find out more about Zero Trust, please don’t hesitate to get in touch – Contact – Greystone Consulting Ltd





